Title: Understanding 203.160.175.158.14001: A Deep Dive into Its Function and Usage
Introduction
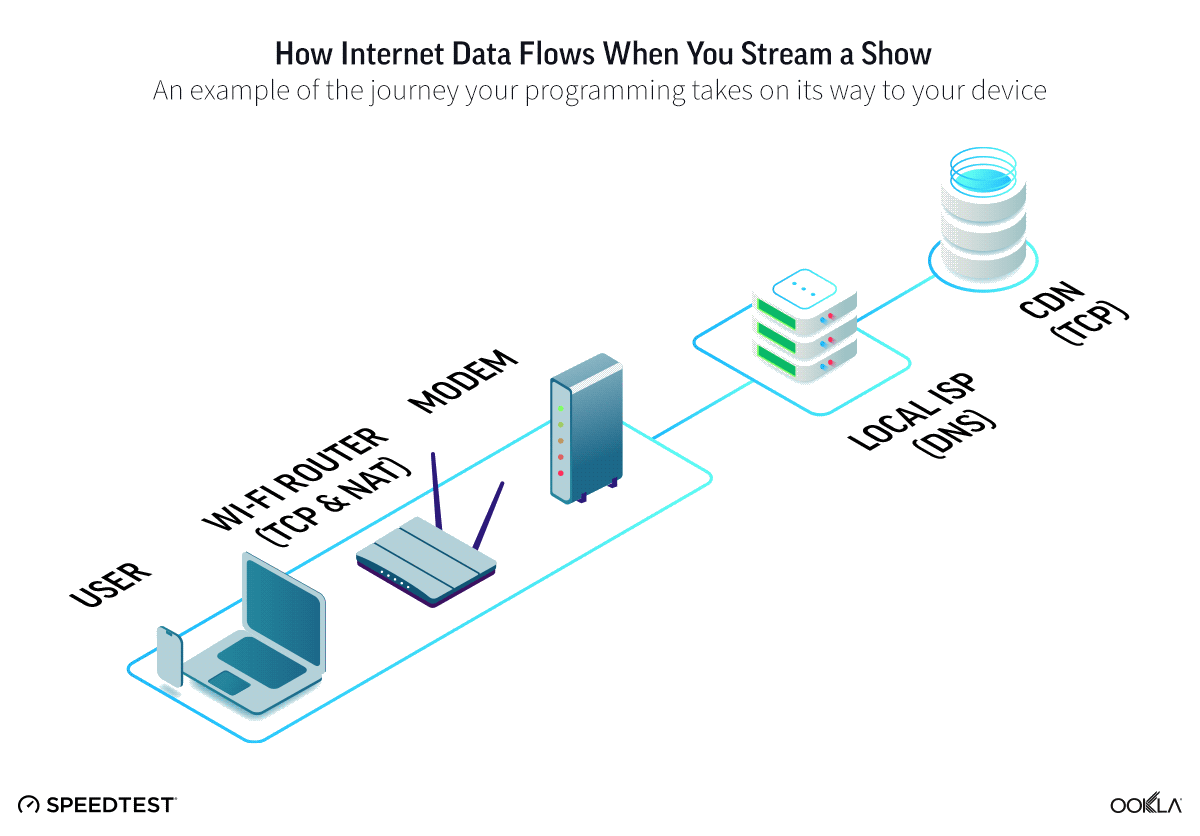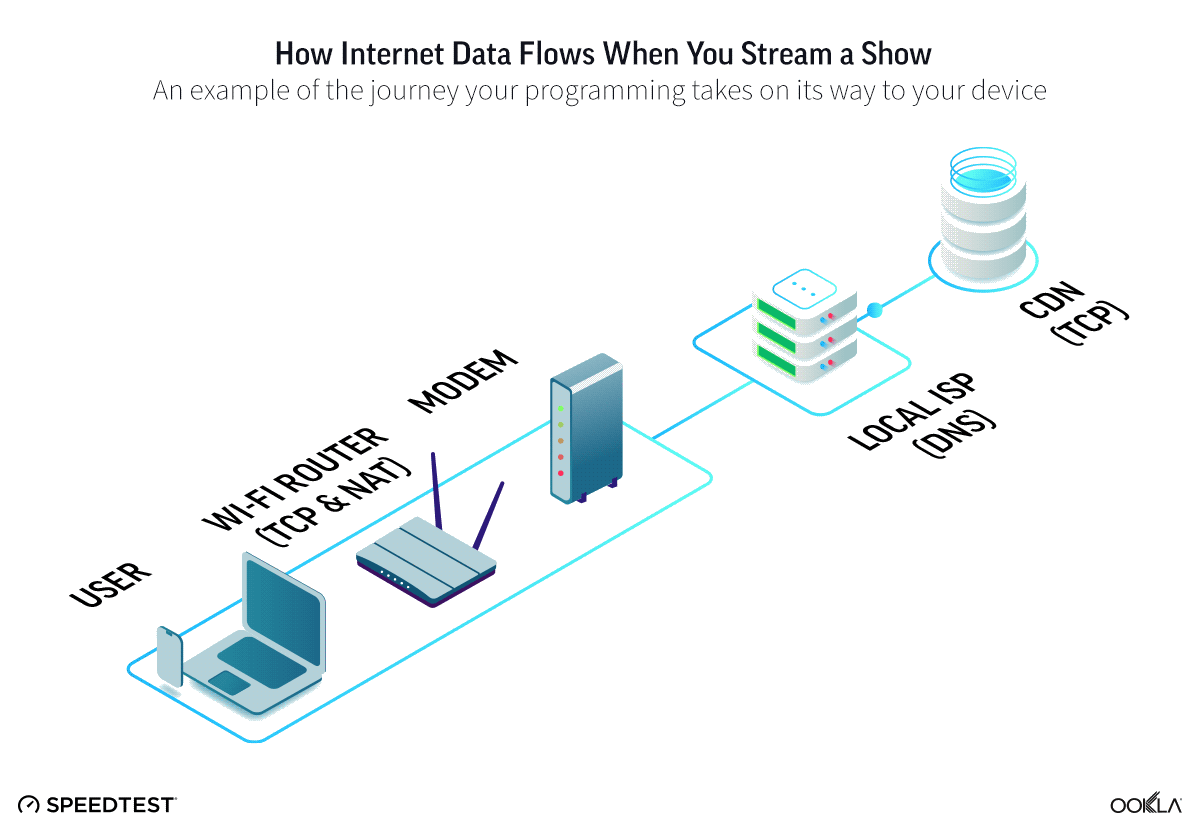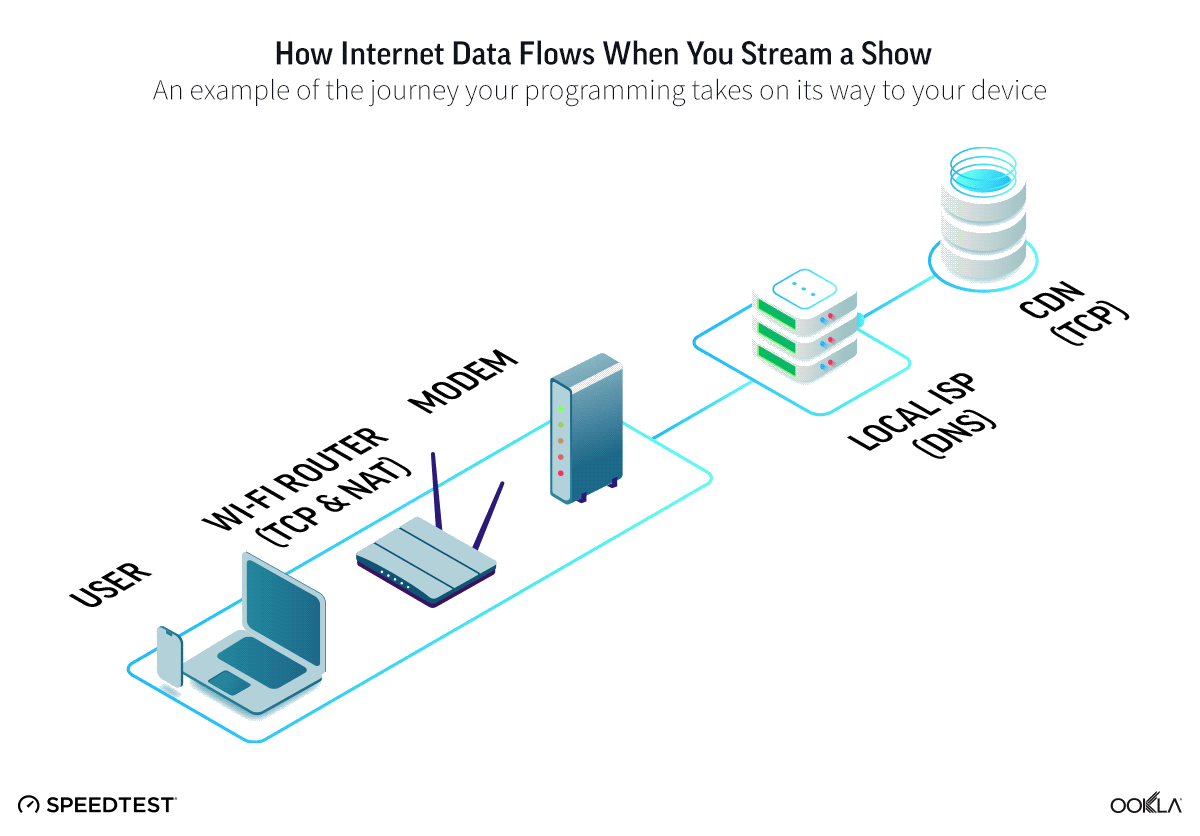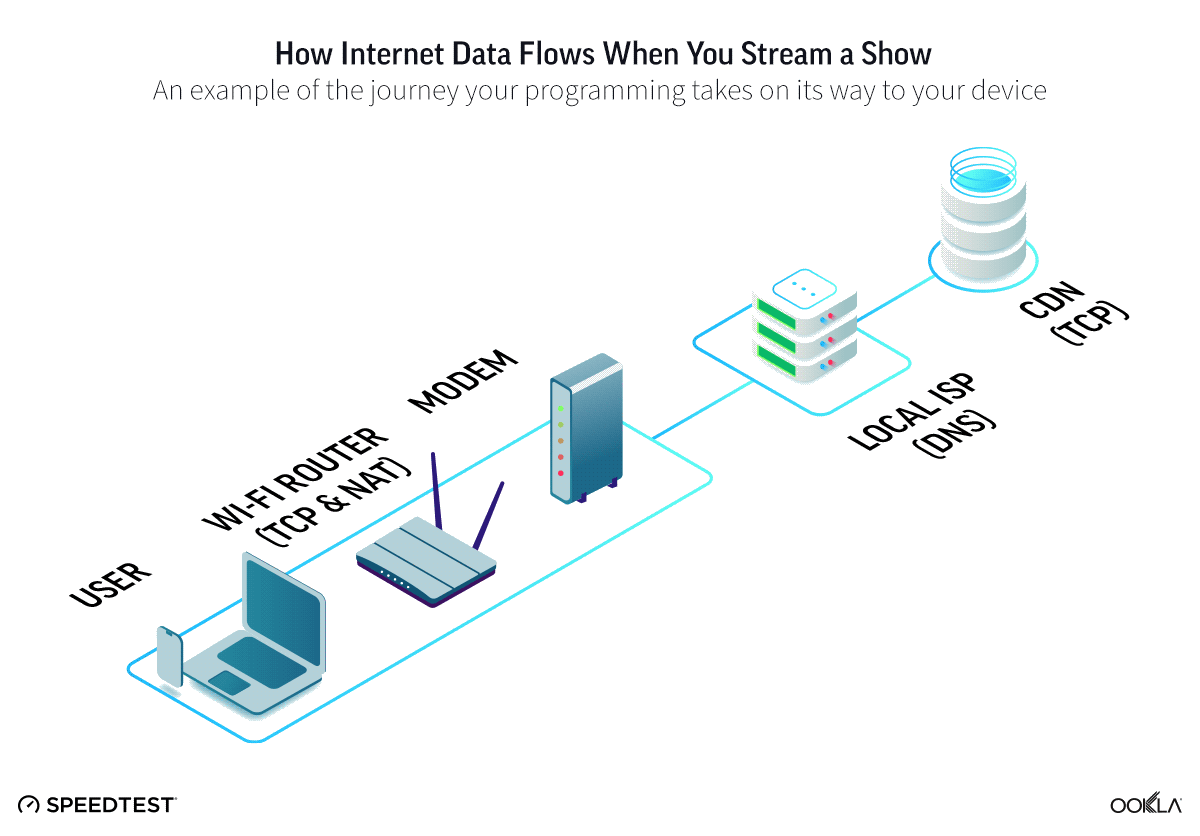
In today’s connected digital world, IP addresses and port numbers play a vital role in maintaining online communication and data flow. The term 203.160.175.158.14001 might seem complex at first glance, but it represents a combination of an IP address and a port — essential components for accessing servers, applications, or internal network systems. Understanding how it works can help users, IT professionals, and developers navigate technical settings more efficiently while maintaining cybersecurity and performance.
What is 203.160.175.158.14001?
The format 203.160.175.158.14001 includes two parts: an IP address (203.160.175.158) and a port number (14001). The IP address identifies a device or server on the internet or a private network, while the port number directs the data to a specific process or application running on that device. Together, they ensure accurate communication between systems. For example, when a browser or software connects to this address, the port tells the server which service or function to respond to.
Understanding the Role of Ports in Networking
Every networked device uses multiple ports to handle different types of communication. Common examples include port 80 for HTTP, port 443 for HTTPS, and port 21 for FTP. The 14001 port in 203.160.175.158.14001 might be associated with a specific custom service or software. In enterprise setups, developers often use higher ports (above 1024) for proprietary or internal applications. These unique identifiers help maintain order and security, preventing data collisions and ensuring that requests are handled by the right service.
Possible Uses of 203.160.175.158.14001
Addresses like 203.160.175.158.14001 can be found in different scenarios, including remote access systems, private servers, or cloud-based platforms. IT administrators might configure such combinations to allow staff to connect securely to internal tools. In some cases, this address could be tied to a specific database, monitoring dashboard, or communication channel. While it’s not commonly accessible to the public, it plays an important role within controlled network environments where precision and restriction are key.
Security Considerations
When dealing with any IP and port combination, cybersecurity must always be a priority. Unauthorized access to an address like 203.160.175.158.14001 can lead to vulnerabilities if the port is left open or improperly protected. To secure such connections, professionals rely on firewalls, VPNs, and encrypted tunnels. Regular audits and access restrictions are also essential to ensure that only authorized users can connect. Monitoring tools can detect unusual traffic or attempts to breach the connection, helping maintain a stable and safe digital environment.
How IT Teams Manage IP-Port Configurations
Managing combinations like 203.160.175.158.14001 requires both technical knowledge and a structured approach. Network administrators use configuration files or management consoles to assign, test, and secure ports. They also document the purpose of each active port, ensuring clarity across teams. Proper documentation helps troubleshoot issues faster and prevents conflicts when multiple services run on the same device. Automation tools can also be employed to check for open or unused ports, further optimizing system performance.
Troubleshooting Connectivity Issues
If a user encounters connection errors with an address such as 203.160.175.158.14001, several factors could be involved. It might be a firewall restriction, incorrect configuration, or temporary server downtime. Running a ping or traceroute test can verify whether the IP is reachable. Additionally, network logs can reveal whether the port is responding correctly. For enterprise users, contacting the network administrator or IT support team is often the safest and fastest solution.
Why Understanding Addresses Like 203.160.175.158.14001 Matters
In the broader context of digital communication, understanding elements like 203.160.175.158.14001 helps users appreciate how data travels securely from one system to another. It reinforces the importance of structure, order, and control in networking. For businesses, it also highlights the need for proper configuration, monitoring, and cybersecurity. A single misstep in managing IPs and ports can lead to disruptions or vulnerabilities, emphasizing the value of continuous learning and awareness in this field.
Conclusion
The combination 203.160.175.158.14001 represents more than just a sequence of numbers — it’s a gateway for precise and controlled communication in digital systems. Understanding how it functions, securing it properly, and managing it efficiently can make a significant difference in maintaining smooth, safe, and reliable network operations. In an era where connectivity defines productivity, mastering such technical details ensures that both individuals and organizations remain ahead in the cybersecurity and networking landscape.



Post Comment